Mastercard’s announcement that it will eliminate 16-digit credit card numbers by 2030 put the payment industry’s impending move to “tokenization” into sharp relief. Here’s what it means — for issuers, merchants and card users alike.
A new payments study by Juniper Research forecasts that the number of “global network tokenized transactions” will double in 2029, shooting to 574 billion from 283 billion in 2025. Specifically, the study refers to “network tokenization” and how the boom in adoption is driven by the increasing risk of credit card fraud.
For many banking executives who don’t work directly in the payments space, the terminology can get hazy because the term “tokenization” can mean multiple things. This is especially so as blockchain technology sees increasing adoption, with its ability to “tokenize” assets.
In the payments area, and in the Juniper research, “tokenization” refers to “network tokenization,” a process involving merchants, card issuers, various payment system third parties, and the card networks themselves that are designed to hide consumers’ card payment account data from fraudsters. As actual plastic cards become less and less a factor in payments — “card not present” transactions, in payments parlance, from online commerce to digital wallets — the potential for fraud increases.
The arguments for network tokenization include increased acceptance when a consumer makes a purchase, a benefit for the buyer, the merchant and the card issuer, all of whom want to see legitimate transactions go through. The intent is to improve authorization rates while reducing the risk of fraud. Juniper’s research suggests that a factor that will accelerate interest in tokenization is Apple’s decision to allow third-party developers to access iPhones’ near-field-communication chip, which could encourage the introduction of more digital wallets.
Let’s explore what the term “network tokenization” means, step by step. The following explanatory article draws on a white paper from Juniper as well as materials published by Mastercard, Visa, American Express, EMVCo, JPMorgan Payments and IBM.
Basics of Tokenization for the Layman
Various animated videos explaining tokenization use images of keys or cartoonish token shapes to symbolize the idea of an abstract item — a string of numbers — that can simultaneously unlock a payment process while being useless to a criminal intercepting the string.
A post by IBM describes a digital token as “a collection of characters that serve as an identifier for some other asset or piece of information.” In the case of payment cards, the idea is to replace the cardholder’s “primary account number,” or PAN, with an equal string of randomly generated digits that, even if discovered en route, would be as useless to a fraudster as the real PAN would be useful.
Don’t confuse tokenization with another method tried in the past to safeguard card account numbers: encryption.
Says the IBM post: “Tokenization replaces sensitive data with strings of nonsensitive (and otherwise useless) characters. Encryption scrambles the data so that it can be unscrambled with a secret key, which is known as an encryption key.”
Network tokenization relies on numbers that contain the same number of digits as the actual PAN. A JPMorgan Payments paper explains that this is done “to enable smooth integration into existing transaction processes” — like for like, in other words.
There are other forms of card tokenization, such as merchant-based tokenization. What sets network tokenization apart is that the tokens are issued by the card networks or parties operating on their behalf, and the tokens issued in this way can travel throughout the payment stream as is. The term used in the field is “interoperable.”
The card networks coordinate technical standardization of network tokenization through an international interindustry group, EMVCo. The organization marked its 25th anniversary in 2024. It was originally founded to provide standards, for now, ubiquitous chip cards, but serves many other payments purposes now, including network tokenization.
The card networks provide multiple pathways for the tokenization of cards that consumers enrol with merchants for purchases.
How Tokenization Works in the Flow of Transactions
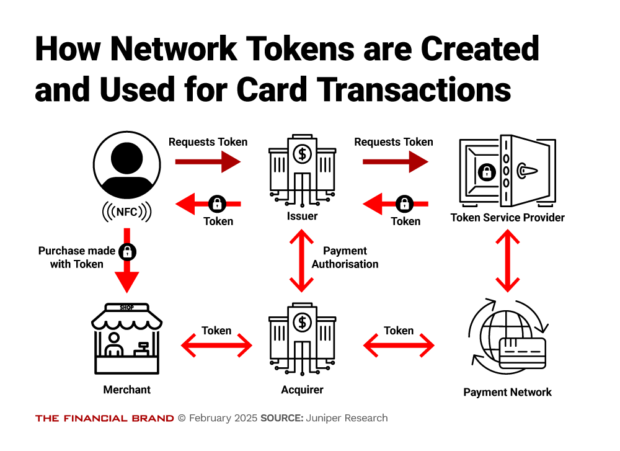
Juniper’s report describes the process as follows, along the lines of the diagram below.
Creation of the network token begins when a consumer puts their card information onto a merchant’s website, into a mobile app, or a personal digital device like a phone, tablet or digital watch. At that time the merchant requests a token, via a token requestor, through the appropriate card network, to the issuing bank. (This part of the process is represented by the dark red arrows.)
If the bank approves the consumer’s account for a token, the card network’s token services provider produces a token to substitute for the PAN. The token is routed back to the token requestor on the merchant’s behalf. The requestor stores the token. (The flow of the token is represented by the bright red arrows.)
The token services provider — such as Visa Token Service and Mastercard Gateway — operates a “token vault” which is where the record of what PANs go with which tokens reside.
Once a token is established — in a purchase, this has all gone on in the background — the transaction is processed as usual. The exception is that the token is used instead of the PAN. The request for authorization of the purchase is routed to the card issuer via the payment network. The approval or denial of the purchase goes back to the merchant via the card network.
Source: THE FINANCIAL BRAND


Recent Comments